DeRISK CRQ (Cyber Risk Quantification)
OT stakeholders, CISOs, CFOs, site managers and executives need better risk insights to optimize cybersecurity and risk management investments.

DeNexus’ DeRISK Platform
DeRISK™ is the only evidence-based, data-driven platform that translates OT cyber risk exposures and vulnerabilities into business metrics such as the financial impact of potential cyber events.
Risk metrics feed into risk mitigation simulations to evaluate how to best allocate cybersecurity resources and budget.

DeRISK empowers executives to make better cyber risk management decisions
DeRISK sets a new standard in industrial cyber risk management. It’s the only solution that quantifies cyber risk using inside-out and outside-in risk data with sector-specific modeling. As a result, executives make reliably informed decisions about cyber risk management and governance. See How >
Key Capabilities
Dynamic Risk Aggregation
Site and portfolio level risk analysis using inside-out data, threat intelligence and contextual outside-in data.
Attack-Path Mapping
Dynamic mapping of potential attack paths and loss events with hundreds of actionable attack graphs.
Quantification of Risks
Expected loss metrics, top drivers of risk, types of loss, and facilities sorted by risk contribution.
Risk Mitigation Simulation
What-if risk reduction simulations to prioritize risk mitigation and optimize cybersecurity controls.
Industry Peer Benchmarking
Peer comparison of cyber risk posture, customized for each industry sector – site and portfolio levels.
Audit and Compliance
Evaluation of cyber risk using NIST CSF, ISO 227001 or DeNexus’ own framework.
Executive Reporting
Access to on-demand, dynamic reports for executive review and governance of cyber risk.
DeRISK Run-Through
DeRISK blends the organization’s internal OT telemetry, including devices, vulnerabilities and controls, with the external threat intelligence and firmographics data used to evaluate the attractiveness of the company to threats actors, to identify most likely attack paths and evaluate the financial impact of potential cyber incidents.
Request DemoElevating Cyber Risk to the Boardroom
DeRISK transforms cybersecurity telemetry into financial risk metrics shareable through executive reports available on-demand to bridge the gap between the control room and the boardroom.
Identify Cyber Threat Sources
By aggregating granular security signals from disparate tools and mapping them to best cybersecurity standards, DeRISK identifies where your cyber risk is coming from and how evolves over time, so that you can better mitigate and thwart cyber threats.
Quantify Risks in Monetary Terms
Cyber risk quantified in monetary terms provides guidance to cybersecurity executives on investment decisions and allow them to track progress with risk reduction over time, showing great cyber risk governance.
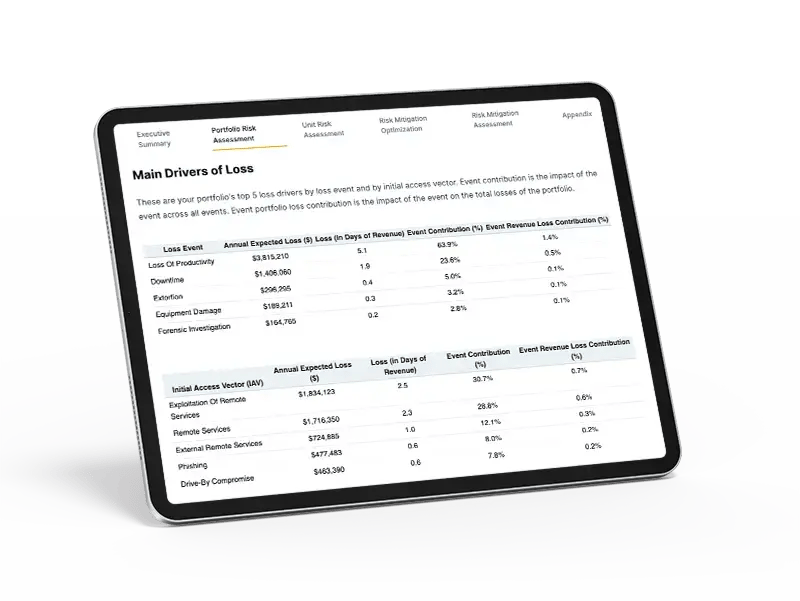
Know the business impact of cyber risk.
Know where to start with risk management.
0
data sources
0
billion simulation runs weekly per site
0
pre-configured risk mitigation strategies
Solve Cyber Risk
Request a demo of the world’s first cyber risk quantification and management platform.
Request A Demo